Kimsuky APT Uses forceCopy Malware to Steal Browser Credentials
The North Korea-linked hacking group Kimsuky has been observed conducting spear-phishing attacks to deploy a new information-stealing malware called forceCopy, according to a report from the AhnLab Security Intelligence Center (ASEC).
Attack Methodology
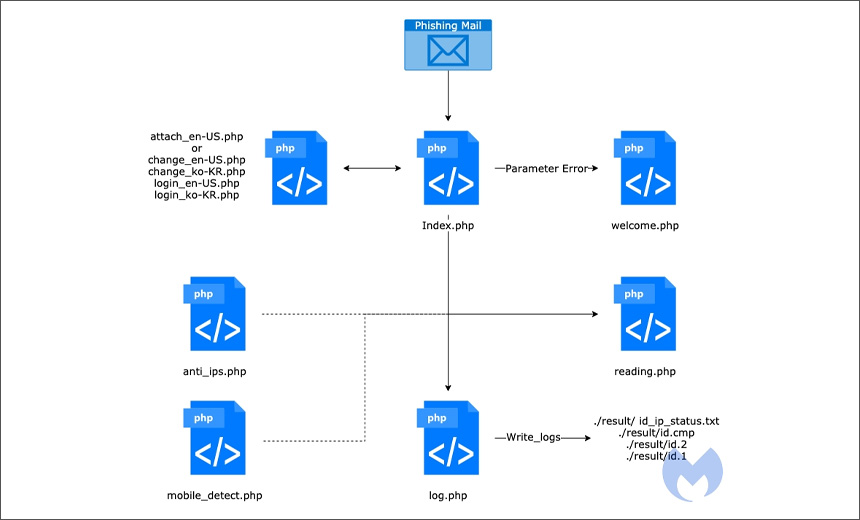
The campaign begins with phishing emails containing Windows shortcut (LNK) files disguised as Microsoft Office or PDF documents. When opened, these files execute PowerShell or mshta.exe (a legitimate Microsoft binary used to run HTML Application files), which then fetch additional payloads from an external server.
Malware Deployment
The attacks ultimately lead to the installation of:
- PEBBLEDASH – a known trojan.
- RDP Wrapper – a modified open-source Remote Desktop utility.
- Proxy malware – enabling persistent remote access via RDP.
- PowerShell-based keylogger – to record keystrokes.
- forceCopy malware – designed to extract files stored in web browser directories.
Targeting Browser-Stored Credentials
Researchers note that forceCopy installs itself in web browser directories, suggesting that Kimsuky is attempting to bypass security restrictions and steal configuration files where login credentials are stored.
Evolving Tactics
The use of RDP Wrapper and proxy malware marks a tactical shift for Kimsuky, which previously relied on custom backdoors for persistence. The group, also known as APT43, Black Banshee, Emerald Sleet, Sparkling Pisces, Springtail, TA427, and Velvet Chollima, is linked to North Korea’s Reconnaissance General Bureau (RGB), the country’s primary foreign intelligence service.
A History of Social Engineering
Active since at least 2012, Kimsuky is notorious for highly targeted social engineering campaigns that can bypass email security filters. A December 2024 report from cybersecurity firm Genians revealed that the group had been using Russian-based services to launch phishing attacks aimed at credential theft.
Mitigation Strategies
To defend against Kimsuky’s attacks, cybersecurity experts recommend:
✔️ Avoid opening email attachments from unknown sources.
✔️ Enable multi-factor authentication (MFA) for critical accounts.
✔️ Regularly update browsers and security software.
✔️ Use password managers instead of storing credentials in browsers.
As Kimsuky continues refining its attack methods, organizations must remain vigilant and implement strong cybersecurity measures to counter evolving threats.